The Ultimate Guide to Anti-Counterfeiting Technologies
The Ultimate Guide to Anti-Counterfeiting Technologies
In this guide, you’ll learn the basics of anti-counterfeiting technologies, how to protect your brand, and how to prevent your product from being counterfeited. By the end, you’ll get an overview of the different security levels of anti-counterfeiting technologies from level 1 (overt) to level 4 (forensic) and be able to build a strategy which you can use to protect your brand.
Counterfeiting- A Global Threat
According to a 2016 report by Global Intellectual Property Center (GIPC), under the auspices of the US Chamber of Commerce, counterfeiting accounted for 2.5% of world trade or a whopping $461 billion USD. Of this, China accounted for over 70% of global physical trade in counterfeit goods amounting to as much as $285 billion USD or 1.5% of that nation’s GDP. Taken together with Hong Kong, this amounts to an astounding 86% of global physical counterfeiting, notching up an annual total of $396.5 billion USD worth of counterfeit goods.
Ukraine, India, Russia and Turkey were the other major sources of counterfeit goods with respective shares of 0.43%, 0.38%, 0.37% and 0.37% respectively.
Counterfeiting has a significant impact on the global economy – resulting in the loss of 2.5 million jobs, as well as more than 60 billion euros worth of tax revenue losses among the G-20 group of economies.
According to the Global Brand Counterfeiting Report 2018-2020, the global figure for counterfeiting stood at a gargantuan $1.2 trillion USD in 2017 and is expected to hit $1.82 trillion USD by the end of 2020. What makes it particularly worrisome is the fact that it includes products ranging from complex defence systems to humble watches.
The advent of the digital age has worsened matters with global losses attributable to online counterfeiting standing at $323 billion USD in 2017. What has also increased is the incidence of technology-driven trademark counterfeiting.
“Measuring the Magnitude of Global Counterfeiting – Erai.”
https://www.erai.com/CustomUploads/ca/wp/GlobalCounterfeiting_Report.pdf. Accessed 21 Jul. 2020.
The losses have been particularly huge in industries like high-end consumer goods ($98 billion USD) on account of both online and offline counterfeiting. The losses incurred by luxury brands by way of online counterfeiting was as high as $30.3 billion USD
Products At Risk of Counterfeiting
While it is very difficult for most people to tell a counterfeit product from a real one, the sheer range of authentic-looking knockoffs are quite extensive. According to the U.S. Customs and Border Protection (CBP), the agency tasked with seizing such goods, the ten most commonly counterfeited products that they confiscated in 2018 were the following:
6%
Consumer Products
7%
Pharmaceuticals & Personal Care/Cosmetics
2%
Optical Media
1%
Toys
1%
Computers and accessories
The dangers arising from the booming counterfeit industry are many and go way beyond quality issues and loss of revenue for brands. In the case of certain commonly counterfeited products, the dangers are of a very lethal kind. Let’s take a look:
- Counterfeit Cosmetics – According to research carried out by Red Points, fake Gucci, Chanel and Lacoste perfumes containing hazardous ingredients like urine and antifreeze were confiscated by the police in New York.
- Counterfeit Auto Parts – According to the US Federal Commission, the counterfeit auto parts industry is annually worth as much as $12 billion USD. That this is a very serious problem with grave implications for people’s health and safety is borne out by the fact that using things like counterfeit airbags can have fatal consequences.
- Counterfeit Pharmaceuticals – The counterfeit medicine industry is valued at a mind-boggling $75 billion USD. According to the World Health Organization, a third of such drugs do not come with any active ingredient, gravely risking the lives of people dependent upon life-saving drugs. The iconic pop star Prince is thought to have died on account of counterfeit pills. There possibly cannot be a more diabolical aspect to the counterfeit goods industry than fake medicines.
Developing an Anti-Counterfeiting Strategy
The prospects of skilled counterfeiters wreaking havoc with a brand’s revenue and prestige is a nightmare for any business. The possibility of this happening to your brand is real and presents a real risk that your brand needs to guard against..
What should your brand do if someone is trafficking counterfeit copies of your products?
This is the million dollar question that you need to answer on an immediate basis. Your brand’s reputation is at risk. When that happens, you have three options, namely:
1. Commence court proceedings to establish that your rights have been infringed and to seek legal redress.
This is something that you simply have to do to not just salvage the already damaged reputation of your brand, but to recoup the financial losses that you have suffered and also to send out a clear warning to potential counterfeiters to steer clear of your brand at the risk of facing consequences.
2. Destroy or request the destruction of the goods from their owner/importer/exporter.
Counterfeit goods can destroy the fair name of a brand owing to their poor quality that can cause harm to the consumers. It is both in the brand’s and consumers’ best interest to get rid of such goods expeditiously. It makes sense to appeal to the people who acquired such goods inadvertently and unknowingly to get rid of them immediately.
3. Improve the security features of your product by implementing anti-counterfeiting technologies. Communicate your anti-counterfeiting strategy to the public.
Help your customers know how to spot fake versions of your product and how to verify genuine ones. For example, you might implement product authentication using –counterfeit QR codes or NFC tags. You might also choose to deploy more advanced anti-counterfeiting technologies like invisible taggants.
What should you do if someone is selling counterfeit copies of your products online?
This is a pretty depressing scenario to come across with and unfortunately it is all too common in the digital landscape. You need to do some immediate remedial and corrective measures. Depending on the circumstances, it may be possible to take a number of concrete steps that can stop and deter such cyber criminals from trying to cash in on your brand’s fair name by selling fake products online. Here’s what you could do:
- A notice could be served to the ISP that hosts the website asking them to take it down on account of the fact that the offending website infringes upon your brand’s copyright and trademark.
- In the event of the website having been constructed on the eCommerce platform of another legitimate business organization, the latter can be asked to block access to the site, selling the counterfeit products, as it is illegal under law.
- Similarly, the payment provider through which the offending website sells its fake products can be contacted and asked to block or withdraw the payment facility, as the offending website is engaged in the selling of products considered illegal under law.
What should you do if someone is manufacturing fake copies of your products?
There cannot be a greater infringement upon the right of a company to carry out its lawful business than have counterfeiters manufacture fake copies of its products with the intention of selling them to its unsuspecting customers. Manufacturers these days can take a number of stringent measures to prevent this from happening. Here’s some suggestions:
- You can use services like the TrackMatriX subscription platform that is a veritable one-stop shop anti-counterfeiting solution. It has a unique track and trace ability that can be leveraged to help your products against counterfeiters. It enables companies to have serialized anti-counterfeit QR codes or NFC tags which can also detect product diversions or unauthorized sale. Both these tools are reinforced with many robust multi-level security features that include overt and covert features.
- You can partner with the police, tax authorities and other law enforcement agencies to take on the organized counterfeit goods industry. The most important aspect of this cooperation can be by way of training these organizations to identify fake products, as well understand the intrinsic security features of legitimate products or anti-counterfeit technologies used.
How can brand owners protect their businesses and customers from counterfeit and pirated goods?
Brandowners can proactively and comprehensively secure their businesses from counterfeit and pirated goods, by leveraging the four different security levels of anti-counterfeiting technologies. The four-tier security pyramid deters counterfeiters from replicating manufactured products.
Level 1: Overt Security Features
These need to be one step ahead of what the counterfeiters might have up their sleeves. Something like a high-resolution hologram or patterns based on the latest and most advanced mathematical algorithms printed onto the packaging is a great example of a foolproof overt security feature.
Level 2. Covert Security Features (Using Ordinary Devices)
Effective covert security features embedded into a product’s packaging include RFID tags and NFC chips that empower consumers to scan and authenticate a product packaging using only their smartphones. You can obtain a high level of security against counterfeiting with just the help of a humble mobile phone.
Level 3. Covert Security Features ( Using Special/Sophisticated Devices)
Considering the lengths to which counterfeiters can go to replicate the products of highly regarded brands, it makes eminent sense for companies to consider using myriad covert security features that require the use of special and sophisticated devices to protect their products. These tools could range from a magnifier to a customized device like a taggant detector. The fact that these security features are covert makes it impossible for potential counterfeiters to get past them.
Level 4. Security Involving Forensics, Taggants & Labs
This offers the ultimate security among anti-counterfeiting technologies available to both products and packaging. Taggant technology has been successfully deployed for a wide range of products as a means of forestalling counterfeiting. Taggants can have unique forensic signatures. What makes this deployment particularly effective is the fact that this form of authentication technology finds acceptance in courts of law on the basis of laboratory-verifiable forensic evidence.
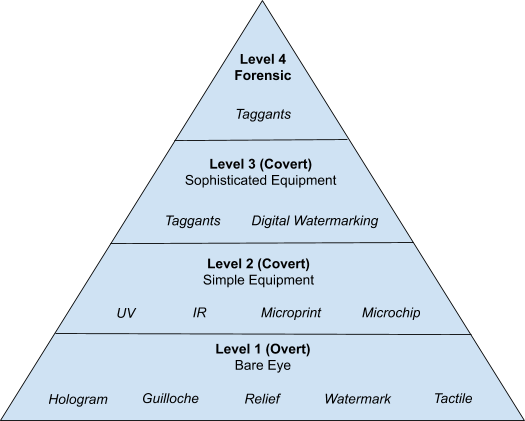
Security Level Pyramid (Four Security Levels)
Overview of Different Authentication and Anti-Counterfeiting Technologies
The counterfeiting industry may be a huge menace for businesses and brands around the world causing monumental losses in terms of revenue and reputation, but the response too has become increasingly effective.
The world has taken note of the grave dangers posed by counterfeiting to companies and consumers alike, and a slew of technologies are being deployed to thwart counterfeits. Let’s take a look at the different anti-counterfeiting technologies in some more detail.
The main purpose behind the use of these anti-counterfeiting technologies is to help authenticate any product by industries, governments, and consumers. The other important reason is their ability to act as a deterrent to those considering counterfeiting the products in question.
A. OVERT TECHNOLOGIES (VISIBLE)
When it comes to Overt security features, their biggest advantage is that they can be authenticated by mere observation without any use of equipment. Visual analysis is the simplest authentication methodology.
These features deter fraudsters from making counterfeit versions of products by being difficult or expensive to replicate. End-users or consumers of products with overt security features also need some information or training in order to recognize these features and to be able to tell the difference between fake and genuine products.
Some examples of overt security features and technologies are the following:
1. Tamper-evident security labels
Tamper-evident security labels provide visible evidence to consumers that tampering has occurred. Here are some examples of tamper-evident security features used in anti-counterfeiting:
a) Tamper-evident microcut labels or security cuts
These labels which are made of polypropylene or paper, have micro cuts and are placed on the closure flap of the packaging. It acts as a security seal to detect if the label is altered or damaged.

Security label with micro cuts or security cuts

Label with VOID tamper evidence (partial release)
b) Void or micro-void labels
VOID labels are labels that, once peeled off, transfer the legend “VOID” onto the surface of the container packaging, leaving clear evidence of the opening, and preventing the seal from being re-adhered without removal becoming evident.
c) Multi-destructible or “eggshell” vinyl labels (or brittle substrates)
These labels are made of a material (brittle substrates) that destroys itself into small parts if an attempt is made to peel them off.

Security label using brittle substrates
2. Holograms
Holograms are also known as three-dimensional images or dynamic images. Holograms incorporates an image with some illusion of multidimensional (usually 3D) construction, or of apparent depth and spatial separation. Holograms can be combined with other security features and can become a powerful weapon against falsifying.

Holographic security label with honeycomb tamper evidence
Optically variable devices (OVD) such as stripes, security foil patches and windowed thread of the types used in bank notes, are a wide range of alternative devices similar to holograms, but often without any three-dimensional (3D) component. They usually involve image flips or transitions, often including colour transformations or monochromatic contrasts. Security foils enable flexible designs by combining various metallic effects with color shifts and dynamic motifs.
Optically variable devices are generally made up of:
- transparent film (serves as image carrier)
- reflective backing layer (usually a very thin layer of aluminium). Other metals such as copper, ZnS, TiO2, and others are also used to give a characteristic hue for specialized security applications.
Additional security features:
- Partial de-metallization – process wherein the reflective layer is chemically removed to give an intricate outline to the image. The partial removal of the metallic layer is a more restricted process and thereby increases the level of security. Single or multiple metallization alloys can be used for the de-metallization feature.
- Ghost reflective image – the reflective layer can be so thin as to be transparent, resulting in a clear film with more of a ghost reflective image visible under certain angles of viewing and illumination.
- Addition of other security features of different levels. For example, there can be three security levels: a first level verifiable by the naked eye (overt), a second level verifiable by portable instruments (covert), and a third level verifiable by laboratory analysis and/or instruments (forensic).
- Machine readable features, e.g. magnetic coding, conductive, taggant and others.
OVDs are an important component to protect important documents such as banknotes, passports, ID documents, certificates, vouchers and products.

Optically variable device security foil illustration
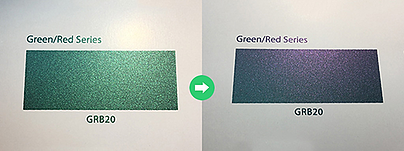
Color shifting ink or optically variable ink
Color shifting security inks or optically variable inks (OVI) show contrasting changes in color when viewed from different angles. These can be used as an overt packaging graphic or as part of a security seal.
5. Fugitive inks
Fugitive inks are special because they are sensitive to materials like water, alcohol, as well as chemical reagents and any other type of physical eradication. These inks disappear or lose shape when in contact with these agents and are deployed in plain offset printing.
Fugitive inks lighten, darken, or otherwise change in appearance over time when exposed to environmental conditions, such as light, temperature, humidity, or pollution.

Example of fugitive ink (1887 British Consular Service tax stamp)
Security graphics involve fine line color printing and use design elements like guilloches, line modulation and line emboss. These can be deployed discreetly as a background or as an overprint area. Security can also be further enhanced by the incorporation of a range of covert design elements, such as microtext and latent images.
- Guilloche: Form of two or even more interwoven fine lines to generate specific patterns by mathematical algorithms. The structure of the design is an intricate and repetitive pattern that can prevent any fabrication or duplication.
- Relief: Line patterns with line width modulation, wavy line patterns and which can enhance convex and three-dimensional display effect of graphics.
- Anti-copy: Combination of special line patterns and graphics to form a graphic in split lines. Split lines appear when the magnifying glass is used. The split lines can serve as anti-copy lines, thereby being blurred out when photo-copies are made from the original document.
- Latent image: Hidden patterns or texts. Integration of parallel lines, Guilloche, and patterns as a hidden anti-counterfeiting to covert information. The hidden image or text appeared when observing the image with a specific optical angle.
- Microtext: The tiny texts can only be viewed by a high-resolution microscope. Any reproduction machine is unable to identify and copy the microtext but in dotted or solid line because of downgrading resolution after scanning or photocopying.
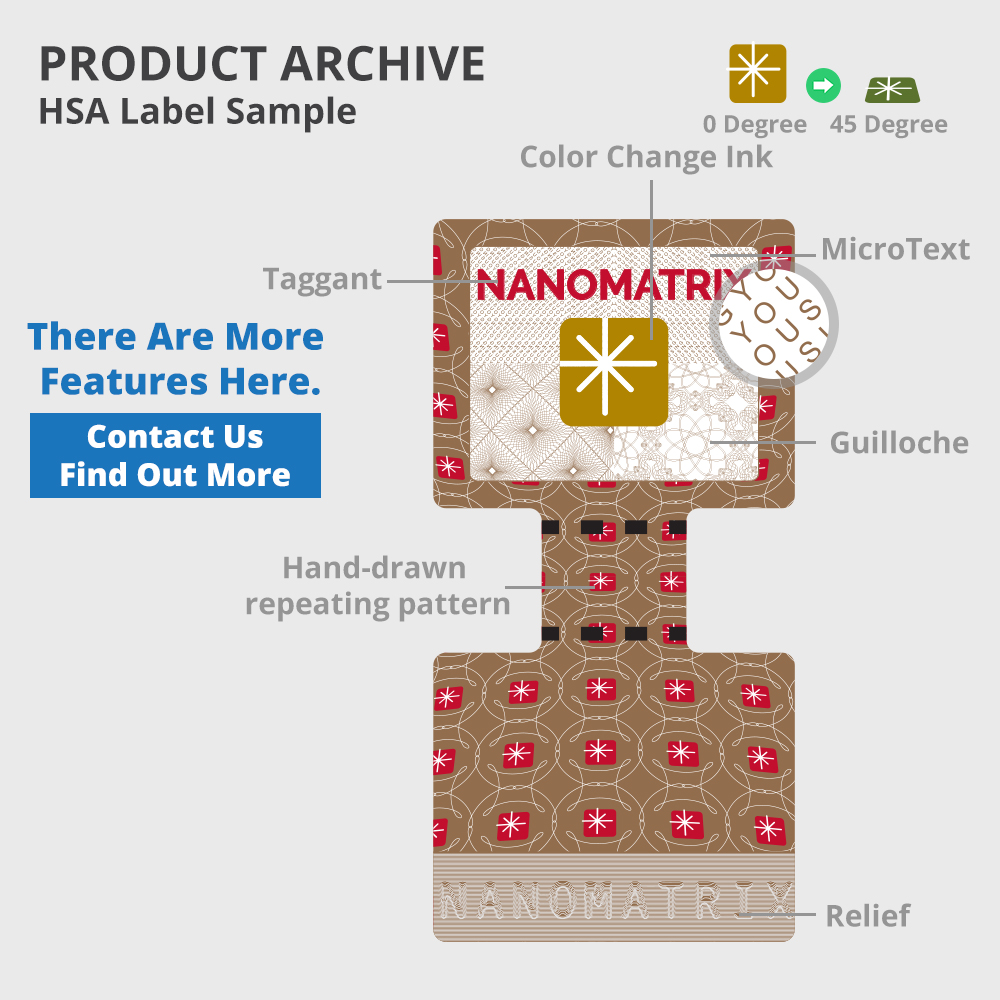
Illustrative example of security graphics design in a high-security label
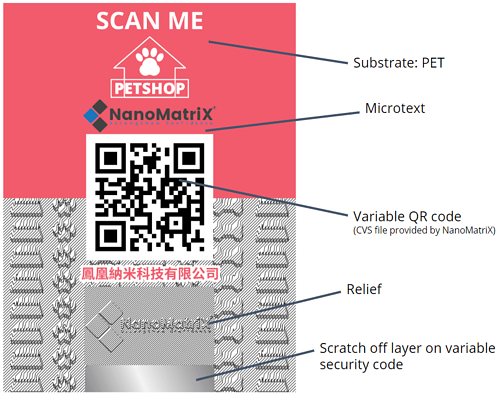
Secure label with scratch-off layer
7. Scratch-off technology
Scratch-off technology consists of a layer of removable ink that can be scratched off (coin or fingernail) to reveal a verification code. This code should be randomized (variable security code), so that criminals cannot predict the codes that will be used. In addition, it must be checked against a database to verify if the product is authentic.
B. COVERT TECHNOLOGIES (HIDDEN)
Covert security features are usually hidden from consumers or end-users. Consumers generally will not be aware of their presence nor will they have the means to verify it.
However, some covert technologies may be used in an overt context by advertising their presence, if it is inherently secure against compromise and the end-users have the means by which to authenticate them.
Covert features are not easy to detect or copy without specialist knowledge, and their details are controlled on a “need to know” basis.
Here are the principal examples of available covert anti-counterfeiting technologies:
1. Invisible printing
Invisible printing – makes use of special inks, pigments, or invisible markings that only appear under certain conditions and can be printed on almost any component. These markings cannot be viewed with the naked eye and simple or special equipment is needed in order to reveal the ink.
a) Luminescent inks/pigments – luminescent inks are not visible within the white light spectrum. This group can include both fluorescent and phosphorescent inks/pigments.
- UV fluorescent ink/pigment has a fluorescing pigment that can be seen when exposed to ultraviolet light of a specified wavelength. Blue short-wave ultraviolet fluorescent ink is widely available and provides only a low level of security unless well hidden. Other colours (yellow, green or red) are more secure, and some combinations produce different colours with short and long wavelengths of ultraviolet light. Ultraviolet-suppressing pigment may also be added to render substrates non-fluorescing, or may be printed over a fluorescing background for subtle effect.
- Phosphorescent inks/pigments continue to emit light for a short period of time after exposure, and can be detected with a reading device.
b) Reactive inks or dyes Luminescent inks/pigments – when subjected to ultraviolet light, vary in color, but these colours are mat and non-fluorescent.
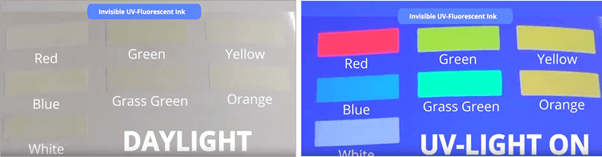
Bright invisible UV fluorescent pigments when exposed to UV light or black light

Phosphorescent powder shown under visible light, long-wave UV light, and in total darkness.

IR Upconverter Pigment Detection with IR Laser Pen (100 mW and 200 mW)
c) Infrared (IR) Upconverter Pigments or infrared fluorescent pigments
Infrared (IR) Upconverter Pigments or infrared fluorescent pigments – can be tuned to very specific wavelengths of invisible light, and are only available from specialist suppliers. They have a high security level. IR upconverter pigments are invisible to the naked eye, yet easy and reliable to inspect using detection systems or an IR laser pen.
IR upconverter pigments are inorganic luminescent particles, which convert incoming invisible IR light to visible light. Depending on the IR upconverter pigment type used, the pigments exposed to IR light emit visible colors such as blue, yellow, orange, red and others.
d) Photochromic inks or photochromic pigments
Photochromic inks are invisible under artificial light and will appear visible once exposed to outdoor sunlight or UV / black light. Photochromic inks change colour when exposed to a specific wavelength of light. They have a high security level if detected via a specific reader. This effect is reversible. Once the ink is not exposed to sunlight or UV light, the ink will return to the transparent appearance within one or two minutes.

Photochromic effect under UV light

Thermochromic pigment color change effect
e) Thermochromic inks or thermochromic pigments
Thermochromic inks and pigments are a type of dye which change color in response to temperature fluctuations. They either disappear or change colour at varying temperatures. Thermochromic inks and pigments can be applied to a variety of products including vouchers, tickets, certificates, tax stamps and others. There are two different categories of thermochromic inks:
- Irreversible inks – once a certain temperature is reached, the color will remain unchanged or permanent
- Reversible inks
There are different types of color change effects in thermochromic inks/pigments:
- Color to invisible
- Color to color
- Invisible to color
- Tri-thermochromic: color to color to invisible
2. Latent image or three-dimensional (3D) intaglio printing
Latent image or three-dimensional (3D) intaglio printing – are composed of horizontal and vertical lines that form, for example, letters, figures or logos. They are revealed according to the angle of incidence of light that, when it hit lines reveals opposed lines arranged otherwise.
Latent images are hidden patterns or texts. They are an integration of parallel lines, Guilloche, and patterns as a hidden anti-counterfeiting covert information. They cannot be copied by flat photocopy systems.
Example of this latent image feature is shown in the Bank of Japan banknotes. When the banknote is viewed from a certain angle, the number “10000” appears on the bottom left of the front side, and the word “NIPPON” (“Japan” in Japanese) on the top right of the back side.


Latent image security feature in 10,000 Japanese yen note

Watermark on 20 Euro banknote
3. Watermarks or filigrees
Watermarks or filigrees – are security features applied directly into the structure of the paper or cardboard during the manufacturing.
Watermarks are drawings (logos, texts, motives, etc.) in the paper structure formed by controlled changes in the paper machine and visible against the light. A watermark is a recognizable image or pattern in paper that appears as various shades of lightness/darkness when viewed by transmitted light (a atop background is viewed when we put in reflected light), caused by thickness or density variations in the paper. Watermarks can cover an entire page or can be smaller and placed on a specific area of a page.
In banknotes, watermarks are recognizable designs that are put into the paper on which the documents are printed, whilst in checks they tend to be specific patterns. These watermarks are normally used to prevent people from being able to make fake copies, and, therefore, to be confident that the banknote or document is authentic.
Specialized printing techniques also make it possible to have printed watermarks that will vanish or appear if a protected document is photocopied or scanned.
5. Digital watermarks
Digital watermarks – are invisible data digitally encoded within graphics elements and verified by means of a reader and special software. Authentication can be achieved remotely using a webcam, mobile phone, or other scanning equipment, but the digital information is not visible to the human eye and attempts to replicate it will be detected by virtue of the degradation of the embedded data.
Digital watermarking is the process of embedding information into a digital signal. In security printing, machine readable data is digitally watermarked into banknotes. Such watermarking can be optically sensed and detected by various devices. In response, such devices can intervene to prevent banknote reproduction. This addresses various problems, e.g., the use of digital image editing tools to circumvent other banknote anti-copy systems.
Digital watermarks and secure graphics can be inserted into digital images before printing security documents.
An example is the EURion constellation (also known as Omron rings) which is a pattern of symbols incorporated into a number of secure documents such as banknotes since about 1996. It is added to help imaging software detect the presence of such a document in a digital image. Such software can then block the user from reproducing banknotes to prevent counterfeiting using colour photocopiers.
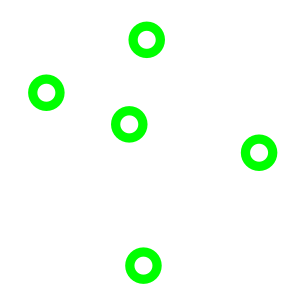
EURion constellation recurring pattern (digital watermark)

6. Hidden marks
Hidden marks – can be printed in areas not normally visible like carton glue flaps, in an unobtrusive manner that is not easy to replicate.
These hidden marks can be printed using specialized print screens, e.g. stochastic screening.
Stochastic screening (Staccato) is a type of digital halftone screening which varies the pattern of dots while keeping the size of the dots constant.
It refers to FM screens, or frequency modulation. This refers to micro-dots (20 micron, 10 micron) that are fixed in size and tone values increase by adding more dots. The dots are rendered in a pseudo-random algorithm making them ideal for high definition details in photography and artwork. The micro-dots are rendered in a ‘weave’ to create very smooth tonal transitions.
7. Microtext / microprint
Microtext / microprint – comprise extremely fine text (1 point letter size or below) which cannot be viewed with the naked eye.
These tiny texts can only be magnified viewed. Ordinary reproduction machines are unable to identify and copy the microtext but in dotted or solid lines because of downgraded resolution after scanning or photocopying.
This is normally visible under low power magnification (x8), but with specialist printing techniques the text can be extremely small, requiring medium to high power magnification (“nanotext”). Microtext can be concealed by printing against a poorly contrasting background, or resembling a keyline or a complex path in a geometric design element.

Microtext “NIPPON GINKO” in 5,000 yen note
Void pantograph (anti-copy design)
8. Anti-copy or anti-scan designs
Anti-copy or anti-scan designs – these designs are largely used with secure documents to prevent them from getting photocopied using halftones. It can also be applied to product packaging as a background tint.
Halftones are normally printed as dot screens for continuous toning, but if fine parallel line patterns are used to achieve a uniform density or tone, these can be resistant to scanning or copying by revealing a secondary pattern that was not otherwise visible.
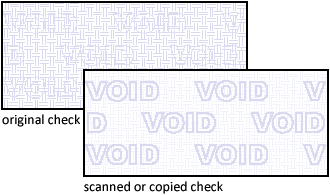
Void pantographs are examples found in checks. A light-colored pattern that’s hard to reproduce gets printed on the document: the halftone screens of the printing process are manipulated to produce a dot pattern that the human eye can’t see but that a wide range of scanners and copiers will detect.
A background design is incorporated in the document that can’t be detected under normal circumstances. But scan or xerox copy that same check and the hidden message — the words “VOID”, “NULL”, “UNAUTHORIZED COPY” or some similar phrase — appears in the image.
9. Security fibrils or filaments
Security fibrils or filaments – are small visible or invisible white light fibrils, which are incorporated into the material intertwined with their most fundamental fibres during manufacturing. They consist of 5 mm synthetic threads (usually nylon) and can be of different colours. They can be distributed throughout the packaging or located in a specific part of it.
They can be detected by ultraviolet light, revealing different colours according to the material. They are placed during manufacturing so that criminals will be limited to copy them.

Security fibrils or filaments visible under UV light
Laser engraved data on identity card (SecureIDNews)
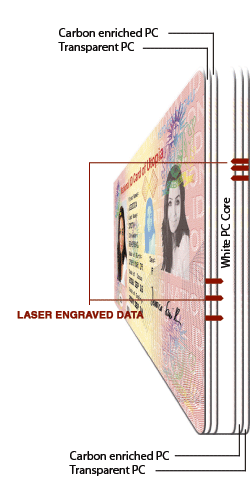
10. Laser Coding / Etching / Engraving
Laser Coding / Etching / Engraving – enables the application of batch variable details carried out by way of special and expensive equipment. It creates recognizable characteristics that may be almost impossible to recreate.
It generally involves burning away the characters from a dark printed panel via a stencil. Laser codes can be applied to cartons and labels, aerosol valves and plastic and metal components, enabling these to be identified.

Laser coding (laser numeration) security feature (KEIT)
11. Distinct Odor
Distinct Odor – micro-encapsulated distinctive odours can be applied as an additive to an ink or coating to provide a unique covert or semi-overt feature.
One particular scent is made up of a few hundreds to a few thousands of odor components. For example, there are 500 different odor components responsible for the smell of coffee and 1000 odor components found in human breath.
Odor-sensing technologies such as those developed by NEC discriminate odor based on the characteristic features of wave patterns of electronic signals, even when odor components and mechanisms are unknown.

Palm-sized measurement module embedded with the olfactory sensor (Image credit: NEC)
C. FORENSIC TECHNOLOGIES
Forensic anti-counterfeiting technologies comprise an extensive range of high-technology solutions that have to be backed up by laboratory testing or field test kits that can help furnish scientific proof of authenticity. At the same time, one needs to make sure that the markers / taggants do not adversely affect the integrity of the product.
Taggants can provide a unique code or fingerprint to authenticate originality. A taggant is a chemical or physical marker added to materials.
Physical taggants come in different forms but are usually microscopic, used at low levels for simple and fast detection in a non-destructive manner. Taggants are uniquely encoded and virtually impossible to duplicate and can only be verified with specialized readers.
These technologies comprise trace chemicals detectable only by very specific reagent systems but not normally detectable by conventional analysis. They can only be detected by specialized taggant detectors, effectively becoming as rapid screening tools providing parameters of chemical identity and concentration.

Chemical taggants incorporated into plastic

Chemical taggants incorporated into plastic
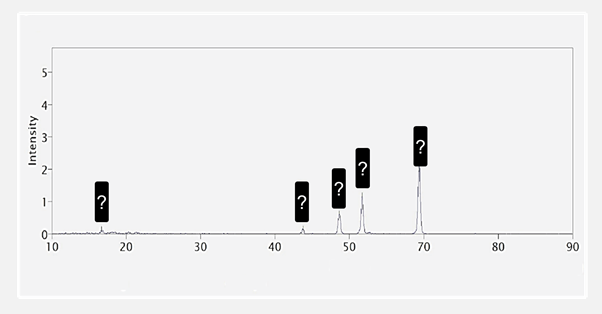
Taggant Forensic Signature – Laboratory Test Result
Taggants can contain forensic features called ‘elemental signatures’. Elemental signatures can be verified by independent material science laboratories. An infinite number of elemental signatures can be generated for chemical taggants.
2. Biological taggants
A biological marker is inserted at exceeding low levels (parts per million or lower) into product formulations or coatings. At such low levels they are undetectable by normal analytical methods, and require highly specific “lock and key” reagent kits to authenticate.
Biological or biomolecular taggants consist of synthetic proteins selected in a high-throughput screen for their functional properties. These functional properties include optical properties and chemical selectivity/affinity.
3. DNA taggants
DNA taggants use natural sequence-coded materials such as DNA for labelling. DNA (deoxyribonucleic acid) is a form of forensic evidence trusted by law enforcement and recognized by international courts around the world.
As DNA provides the blueprint for all of biology, the information content is massive and highly customized. DNA is a linear polymer of extraordinary molecular weight that stores its information as a sequence of infinitely variable organic bases. Botanical or plant-based DNA are often used as taggants.
Highly specific DNA recombinant “lock and key” reagent systems can be applied to packaging by a variety of printing methods. They require a “mirror image” strand to effect the pairing, and the reaction is detectable by a dedicated device.
DNA markers are usually printed in a defined area. A second testing liquid is used to prove the authenticity of the product. When the customised DNA pen applies the identifying liquid substance on the printed area either a colour change or luminescent reaction proves the authenticity.
4. Isotope ratios
Naturally occurring isotopes can point to the source of a compound with the help of myriad types of mass spectrometry.
Stable isotope ratios are known to reflect geographical variation and have therefore been widely used to trace the provenance of various food or agricultural products.
The content of selected elements (trace elements and rare earth elements) in agricultural products reflects the growth conditions in the particular environment. Furthermore, the isotope ratios (e.g., carbon, hydrogen, nitrogen, sulfur, strontium, and lead) can provide uniquely representative fingerprints, enabling discrimination of the origin of food samples.
With advanced analytical procedures such as cavity ring-down spectrometry (CRDS) and stable isotope-ratio mass spectrometry (SIRMS), isotopic composition of any food sample can be obtained and the geographical origin successfully identified.
For example, pure orange juices of Asia, Australia and New Zealand origin have distinctive oxygen isotope 18O values depending on geographical location, which give an indication of where the juice is from. These isotopes are also used to ensure the juice is fresh and not made from concentrate where water has been added to dilute the juice.
Carbon isotopes 13C are also used to investigate if the label claims of “no sugar added” are true or false. When cane sugar is added to sweeten juice, the carbon isotopes of the juice become more positive as cane sugar has different isotope values to the natural fruit sugars found in juice. By comparing the 13C values of the juice with washed pulp, the amount of cane sugar added to a non-compliant product can be estimated.

Carbon and oxygen isotope ratio analysis of pure orange juice
5. Micro-taggants
These are microscopic particles carrying coded information that can uniquely identify each variant with the help of an examination under a microscope. This may take the form of alphanumeric data depicted on small flakes or threads, or of fragments of multi-coloured, multilayered laminates with a signature colour combination. These may be embedded in any part of the medical product, in the adhesives, or directly applied to packaging components as spots or threads.
CONCLUSION
What has given rise to the adoption of anti counterfeiting measures is the fact that globally there has been an increasing call for regulation. Let’s look at a few examples of this.
| Industry | Region | Regulation | Measures Required |
|---|---|---|---|
| Pharmaceuticals | U.S.A. | DSSCA | Serialization and traceability |
| Pharmaceuticals | E.U. | HMD | Serialization and tamper evident solutions |
| Tobacco | Global. | FCTC | Traceable tax stamps |
| Foods | Global | Product traceability | |
| Crop Protection | India | Labelling | Hologram and barcode |
The world’s anti-counterfeiting, authentication and verification technologies sector is poised to grow from $105.9 billion (USD) in 2018 to $184.6 billion (USD) in 2023 clocking a compound annual growth rate (CAGR) of 11.8% in the years 2018 to 2023. The major factor driving this growth is innovation.
A case in point is signature DNA marker packaging materials used to counter counterfeiting of pharmaceutical tablets.
DNA based anti-counterfeiting measures are far more effective than digital coding in that they allow for way superior encryption. Other things to watch out for are anti-theft tags as well as smart labels equipped with real time tracking.
While anti-counterfeiting technologies have come a long way, their continued success will always depend upon their being several steps ahead of those who make a living from counterfeiting. This is a race that the former will have to keep on winning.
The good news is that all the stakeholders including manufacturers, suppliers, retailers, governments, law enforcing agencies and the consumers have woken up to the immense dangers posed by the counterfeit goods industry and have stepped up to the plate to fight it. It is eminently possible to largely eliminate this scourge if the global will and resolve to do so stays steadfast.
