Different Types of Barcodes
When it comes to barcodes, there really is a very large number of them to choose from. From deciding between 1D and 2D barcodes to zeroing in on the type that is ideal for one’s products or inventory, it is not really that simple to select the one that is just right for one’s business. Let’s look at the different types in a little detail here:
One Dimensional or 1D Barcodes

These barcodes are characterized by changing widths and spacings of parallel lines that are representative of specific data. Among the better known of such barcodes are UPC and EAN codes. UPC barcodes are typically used to help label and scan consumer goods-something that you see at points of sale around the world. The UPC-A comprises 12 numerical digits whereas UPC-E boasts of six encoded such digits.
EAN barcodes are similarly used in the retail industry to help label and scan consumer goods at points of sale around the world, particularly in Europe.EAN 13 barcodes comprising 13 digits are more commonly found, while EAN-8 comprising 8 digits are better suited with products which have restricted space.
Code 39 barcodes are primarily used in the automotive industry, as well as by the U.S. Department of Defense. It uses both numbers and characters and as its name suggests can encode only 39 characters.Their large size might render them unsuitable for small products, but they possess the advantage of being able to be decoded by any kind of barcode reader. That provides them with a fair measure of versatility.
Code 128 on the other hand comprises a high density 128 character encompassing ASCII set capable of storing a large amount of information and therefore ideal for the supply chain industries like shipping. Other types of 1D barcodes are ITF Interleaved 2 of 5 customized for the packaging industry, Code 93 is suited to retail, manufacturing and logistics industries, Codabar for the logistics, healthcare and education sectors, the GS1 databar for retail and healthcare and MSI Plessey for the retail industry.
2 dimensional or 2D barcodes

These types of barcodes are characterized by the use of two dimensional shapes and symbols to represent data.These possess the ability to hold more data per unit area than linear 1D barcodes. 2D barcodes include new types like QR Code as well as PDF4117. These codes are better also on account of the fact they are scannable even after suffering damage in the shape of ripping and scratching- a common enough occurrence in the daily handling of products.
QR codes are ideal for tracking as well as marketing purposes. Cases in point are magazines, business cards and advertisements. These are also great for the retail and entertainment industries. Datamatrix codes are another type of 2D barcodes that are great for using in the case of small items, as well as documents making them ideal for the electronics and retail industries, as well as the government. PDF417 codes are ideal for use by the logistics industry and the government on account of its immense ability to store large volumes of data like fingerprints, signatures and photographs.The extremely space efficient AZTEC bard codes are used primarily in the transportation and healthcare industries.
What is a QR Code (quick-response code)

A QR or quick response code describes a kind of barcode that can be conveniently read by a digital device. Information is stored in the barcode by way of a series of pixels contained in a grid in the shape of a square. A QR code is a handy and flexible way of tracking products as they move across a supply chain. Its unique attributes make it ideally suited for deployment in marketing and advertising activities.
Static vs Dynamic QR Codes
A static QR code, as the name suggests cannot be edited after it has been created. It is ideal for use in situations where there is no need for any information in question to be updated. These are also not suited in situations where you might want to track interactions. One can create various types of static QR codes like website, email, SMS, Wi-Fi, and VCard QR code.These types of QR codes are eminently suitable for use in the case of visiting cards, email signatures and one time campaigns or events.

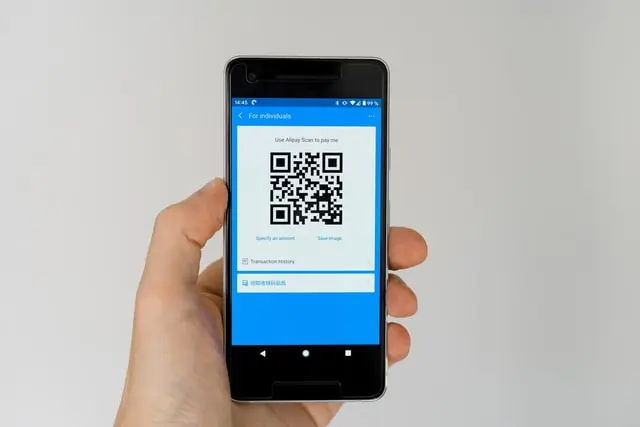
A dynamic QR code on the other hand can be changed in real time allowing one to update things like URLs and 404 errors. This means that one doesn’t need to reprint QR codes every now and then as in the case of static QR codes. Besides, one is empowered to closely track information like the number of times the QR codes get scanned, the kind of operating system used in the process, the location and so on. You can also easily edit your campaigns, as well as leverage these in conjunction with traditional marketing tools like print and TV ads and pamphlets.
Problem: QR Code Security Issues
Though QR codes are used extensively across industries, they do happen to be vulnerable to attack both by way of human interaction, as well via automated systems. This is largely on account of the fact that humans cannot distinguish between a valid, manipulated or cloned QR code and may become a victim of phishing. Automated readers on the other hand become vulnerable when input data has not been adequately sanitised.
Hackers these days possess the ability to embed various kinds of malicious URLs capable of embedding malware into a QR code, which can then make their way into a mobile device via the process of scanning and thereby extract confidential data. Alternatively, the hacker could embed a malicious URL into a QR code that would lead to a phishing site that asks the unsuspecting user to share their credentials, which could then be put to criminal use. So danger in a sense, literally, lurks around every corner, when using QR codes.
Solutions
Anti-counterfeit Invisible QR Codes Using Taggant Ink
One of the best ways of getting around the problem of security threats emanating from the use of QR codes is to use MatriX-Mark™ DOD inkjet technology that is empowered by inorganic security taggants. This provides both covert and forensic security to documents and has seen wide application across a range of cards as well as security documents. In terms of legally enforceable security, MatriX-Mark™ DOD inkjet technology can be further bolstered with the help of an additional impossible to counterfeit security feature. This enables forensic validation using standard laboratory testing procedures even decades hence.
This cutting edge ink-jet technology has applications across the pharmaceutical, electronic components, automotive parts, consumer electronics, tax, excise and revenue stamps, security labels and so on.
TrackMatriX-Lock Code (Anti-copy QR Code)
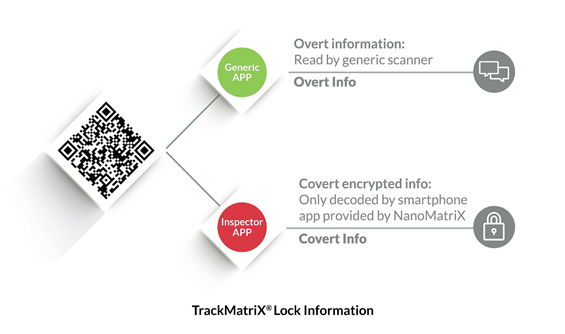
This technology comprises a highly secure cutting edge anti-counterfeit QR code embedded with both overt and covert information. The TrackMatriX-Lock QR code technology is patented for its unique anti counterfeiting and forgery abilities. The deployment of this technology enables one to enhance one’s consumer engagement in a major way.
Besides, it can be used by any consumer who has a smartphone. The code delivery can be via digital means or by way of custom designed security labels. Not only is it impossible to replicate the number sequences, one can implement projects in a matter of weeks and not months. This is one security technology that does not even require you to use security ink, as the standard 300 dpi print resolution suffices.
TrackMatriX-Lock can be scanned using a dedicated inspection app. Alternatively, one can use the decryption module that can enable the reading of secret information with the help of Android, iOS apps, web apps or logistics devices. One can even carry out offline verification.
This technology is capable of being integrated into the TrackMatriXⓇ SaaS platform and implemented by way of security labels. This technology has been used by brand owners across industries including Fortune 500 companies. It has also been deployed by government agencies like the Ministry of Finance, the Department of Motorized Vehicles (DMV), certification bodies, and several universities and educational institutes.
QR codes are a great enabling tool, as long as they have been secured against any hacking threats. Thankfully, with security technologies like those described in the articles being easily implementable, this is not an insurmountable problem.
